Analysis2022-12-30
Defrost Finance Event Analysis
2 Minutes Read

BradMoon
Security Operation / Audit
Summary
An analysis of the Defrost Finance project hack that occurred on December 23, 2022. The hack involved a re-entrancy attack and a rug pull, resulting in the loss of over $12 million. This post provides transaction information, attack processes, and an analysis of the vulnerabilities that led to the hack. MetaScan has the ability to scan for these types of risks.
Background
On December 23, 2022, a re-entrancy attack (V2) was conducted on the Defrost Finance project on AVAX and the hackers gained $173,000. Immediately following, on December 24, 2022, the project owner performed a Rug Pull (V1) with damage estimated at over $12 million.
On December 26, 2022, Defrost Finance stated that the hackers involved in the V1 hack (Rug Pull) had returned the funds.
Transaction information
Re-entrancy attack
Attack transaction:
0xc6fb8217e45870a93c25e2098f54f6e3b24674a3083c30664867de474bf0212dAttacker Address:
0x7373Dca267bdC623dfBA228696C9d4E8234469f6Attacker contract address:
0x792E8f3727cad6e00c58d478798F0907c4cEC340Victim contract address:
0xfF152e21C5A511c478ED23D1b89Bb9391bE6de96
Rug Pull
One of the transactions for modifying the prophecy machine.
0x6307fdc4c7cce0c06a477db59a6ad378eb674cf1c902bd1b3748408926b2582dMint transaction:
0x69e9088b9fa395e8a4fca360c74ea86039510422a0fbbb98cae6872da14e8de2Developer Address:
0x3cd5854fe3a13707b7882d8290d3cae793a7751aLiquidator Address:
0x6F31EB634ABa6921fBf15fc9aA6E08f11348f64fProject owner contract address:
0x5a733eb741bc080abae9bf3adaed9400416932f0
Attack process
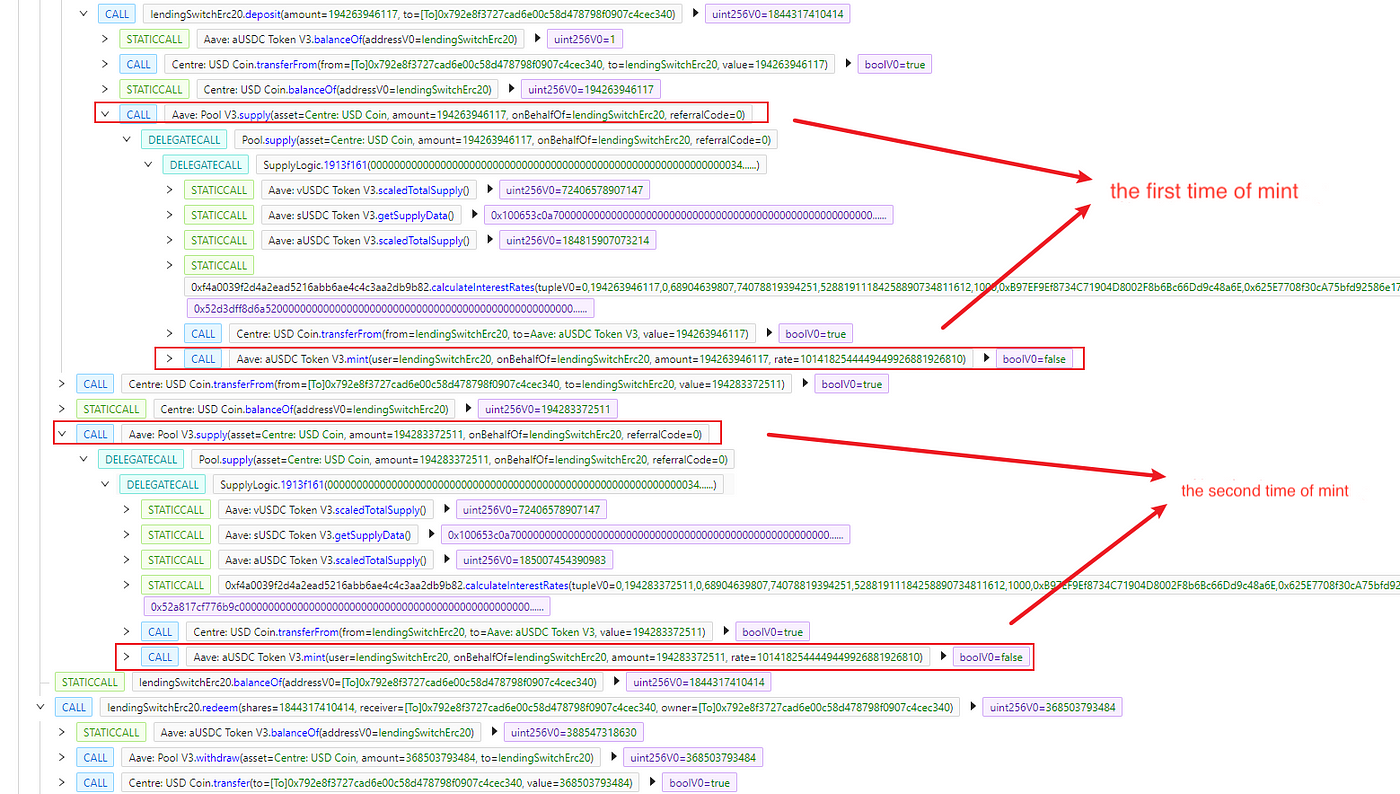
Re-entrancy attack
-
The attacker deploys the attack contract and uses the swap function in JoePair to call the flashloan of LSWUSDC by passing the calldata.
-
Rewrite the onFlashLoan function in the attack contract and call the deposit of LSWUSDC in it to repeat the coin minting.
-
Drained out the entire amount of coins minted twice and return the amount of flashloan, leaving $173,637 as proceeds.

Rug Pull
-
The project owner calls the setOracleAddress function to manually set the malicious prophecy machine for the Collateral Vault of a large number of tokens.
-
Call the joinAndMint function to mint fake collateral tokens.
-
Malicious liquidation.
https://miro.medium.com/v2/resize:fit:1400/0*JzjVo3xIOa6R5qmU
https://miro.medium.com/v2/resize:fit:1400/0*HILNZ4v5w57uterh
Analysis of the attack
Re-entrancy attack
In the code, the lack of protection against re-entrancy in the deposit and flashloan functions leads to the attacker being able to re-enter via onFlashLoan. The attacker re-enters the deposit through the malicious contract, and both the _deposit function and the flashloan function make calls to the onDeposit function, which performs the coin minting operation, which allows the attacker to repeatedly mint coins and gain excess profit.
https://miro.medium.com/v2/resize:fit:1226/0*n7G63vClbxUMjf1y
https://miro.medium.com/v2/resize:fit:1286/0*L3g5Z3_jOuCIQ-1a
https://miro.medium.com/v2/resize:fit:1390/0*Miyrv9E3_DxU9yQL
Rug Pull
After the attack occurs, the project owner accidentally modifies the Oracle address. However the clearing logic is dependent on the Oracle address to get the price. This leads to a malicious liquidation by the project owner using the liquidate function.
https://miro.medium.com/v2/resize:fit:1400/0*kZBRhpsJfwrLU_jn
In the setOracleAddress function, a fully centralized method (multiple signatures) is used to determine if the Oracle can be changed.
https://miro.medium.com/v2/resize:fit:1012/0*2cIyI1eCu7WieKa-
https://miro.medium.com/v2/resize:fit:1390/0*p7jfHPgYZoVsR91F
MetaScan can scan for this risk
MetaScan was able to scan for this re-entrancy vulnerability and given two vulnerability reports with suggestion solutions.
- Unchecked target and call data, i.e. this attack is caused by not checking the receiver and calldata passed in by flashloan. The report can remind developers to always pay attention to external incoming parameters for problems.
https://miro.medium.com/v2/resize:fit:1400/0*MPfu18Hp02GDA_pX
- Re-entrancy vulnerabilities, i.e., potential re-entrancy attacks. This report reminds developers to always be aware of potential re-entrancy vulnerabilities in external calls.
https://miro.medium.com/v2/resize:fit:1400/0*1rcCOoPtCNoIQV5r
Reference Links

BradMoon
Security Operation / Audit
Share this article
Summary
An analysis of the Defrost Finance project hack that occurred on December 23, 2022. The hack involved a re-entrancy attack and a rug pull, resulting in the loss of over $12 million. This post provides transaction information, attack processes, and an analysis of the vulnerabilities that led to the hack. MetaScan has the ability to scan for these types of risks.